 People say there are always two classes of technology users; those who take and use technology the way it is brought to them, no questions or complaints, while others who want to indulge deep into the very essence of what’s being offered, and want to empower themselves with everything to take the maximum out of that technology. This rule of thumb holds true for mobile phones as well. The power user crowd has always been different from the average.
People say there are always two classes of technology users; those who take and use technology the way it is brought to them, no questions or complaints, while others who want to indulge deep into the very essence of what’s being offered, and want to empower themselves with everything to take the maximum out of that technology. This rule of thumb holds true for mobile phones as well. The power user crowd has always been different from the average.
If you want to skip the details and get straight to the rooting process, feel free to head over to our guide on how to root your Android phone or tablet device.
Back from the old Windows Mobile ROM cooking days, people have been questioning limitations of every device and finding workarounds. When iPhone was launched back in 2007, the power user (a.k.a hackers and geeks) side of the users quickly realized the true potential the device held, and the cruel software limitations that Apple had sealed it with. What became ‘Jailbreaking’ on iPhone was quickly translated to other platforms as well, and when the world saw the first Android back in 2008, the same concept got adapted there too.

Android, despite being open source, still did not give a user complete control over the device. This laid basis for many potential abilities remaining dormant, and subsequently Android devices began to get ‘rooted’. Now this begets the question, why root? With so many Android-based handsets out there now, this question has become even more important.
Rooting essentially means gaining root-level access to your device. Those who have used Linux OS will easily understand, but for users like me who have been loyal to Microsoft’s operating system all their lives, this means that by rooting your device you get complete control over what should remain in the device and what not. Rooting means you are the master and in control, not to mention the fun of it.
Hence, here’s a list of my top 10 reasons (in no particular order) that I consider worthy of rooting your device for.
Performance Update
There are just too many flavors of Android in the market, with every OEM or carrier adding their own personalization and customization to devices. While they may appeal to some, they do not let the device take full advantage of what the hardware is capable of. With root access, you can actually tweak the OS to behave entirely differently, and with infamous developers like Cyanogen working on custom ROMs and mods, people have actually reported performance boosts. Take the G1 for example. The device never got 2.1 officially, but thanks to Cyanogonmod G1 owners can not only the tastiness of Eclair but also report much better performance than the stock ROMs.
Hardware/Software Interaction
Most Android devices come with hardware that is fairly heavily capable, yet the OS limits them and becomes the bottleneck. By rooting, you actually remove the bottleneck and hence can take full advantage of your beloved Android. For example, overclocking a device’s CPU is fairly simple and rather safe thanks to many third-party apps, yet the OS does not allow it natively, and hence overclocking can only be done with a rooted phone. Or suppose you want to use your mobile’s LED as flashlight (HTC Desire, anyone?) but cannot because HTC won’t allow it? Rooting will allow you to bypass this limitation!

APPS2Sd
One of the most talked-about feature (or disadvantage) of any Android device is the limitation where you can install applications only in the phone’s internal memory and not the SD card. While Google may reason that SD cards are slower in general and cannot run apps as effectively as internal memory, fact of the matter is that most Android devices do not come with massive internal storage spaces, and hence greatly limit the number of applications that can be installed at a time. With rooted devices, you can use Apps2SD, which will copy ALL your applications to a ext2/3/4 formatted SD card an will also store future builds in card. Freedom to choose!
Unavailable Features
When Google brought forth the Nexus One, one of the aesthetically pleasing features was Live Wallpapers. Unfortunately, most of the Android phones vary so greatly, that despite the hardware being compatible with Live Wallpapers, the software won’t allow them to run. My Samsung Galaxy Spica is a perfect example. The handset’s hardware can easily handle Live Wallpapers, yet Samsung chose to exclude it. Thanks to rooting, you can have them on your device as long as hardware allows.

EXTRA APPLICATIONS
Folks at XDA-Developers have created a wonderful application, SetCPU, which allows easy overclocking of various Android CPUs. However, due to the permissions required for such level of operation, a superuser access is necessary, and that can come only from a root access. This is just one example. The internet is flooded with many such applications that remain useless unless you have rooted your phone.
Multitouch
If you have ever typed on an iPhone, you would always remember the smooth, fast typing action that you achieve on that amazing keyboard. Or if you can recall that pinch-zoom actions. These are the products of a multitouch screen.
While most Androids can deal with multitouch, various manufacturers have decided to omit it in their devices. This is not always because the hardware is incapable, but because the software does not let it happen. This becomes even more irritating when you see that HTC Hero had multitouch input support back from the Android 1.6 days, but more modern more powerful 2.1 devices never got it (again, my Spica).
Thanks to rooting, it has become possible to get multitouch input in various devices, most notably the G1.
WIFI AND Bluetooth Tethering
After having rooted your device, you can also use WiFi or Bluetooth tether to share your cellular data connection with your laptop or PC. The application works with ad hoc connections and will get you up and running online on your laptop in no time. Similarly, tethering can also be achieved over a Bluetooth connection. You may check out the app in question here, but remember, rooted-phones only!

Better Keyboard
I have expressed before and I will say again; I do not dislike the Android keyboard. However, it just isn’t enough. HTC, with their SenseUI, brought to their devices the revered HTC IME keyboard which had predictive text input, and made typing a breeze. Since it was an HTC only keyboard, people with phones from other manufacturers were left blindfolded. Again, the root-developer community ported the keyboard for all platforms, making possible for all rooted phones to take advantage of the better input method.
APPS From Other Builds
Almost every build of Android OS differs from others when it comes to default apps. G1 hasn’t got the same stuff as myTouch 3G; Nexus One differs from HTC Desire. What’s more, these applications from one build cannot be ported to another. Hence you are stuck in more than one ways. However, with custom ROMs, the developers usually gather the best of the lot in one complete package, that would leave a user satisfied, not craving. And to get these custom ROMs running on your phone, you need root.
Because You Can!
I am serious, I consider this a reason. You have a powerful, capable device that you have paid for. You should have the right to modify or change it in any way you like. The device is your property, and you would naturally want to see it working at its maximum potential. Hence the point of rooting.
With the latest Froyo announcement at Google’s 2010 I/O conference, most of these reasons may become useless. But Froyo will not be pushed for all devices, at least not immediately. While it will aim to reduce the fragmentation in Android division, until it happens, a rooted device is the only option you have.
Last, please do remember that rooting voids your warranty. Although you can always go back to a stock version of the OS, it is risky business, hence proceed with caution.
Start rooting
Now that you have learned all about what rooting is and why you should root your phone, head over to our guide on how to root your Android phone or tablet device and start rooting!





 A few days before the UN climate summit in South Africa, as happened on the eve of the climate summit in Copenhagen in 2009, a group of internet hackers sent to a file with 5000 private emails of some leading researchers at the University of East Anglia, UK.
A few days before the UN climate summit in South Africa, as happened on the eve of the climate summit in Copenhagen in 2009, a group of internet hackers sent to a file with 5000 private emails of some leading researchers at the University of East Anglia, UK. 


 Men are more likely than women to be deceived and fell into schemes of data theft when using social networks like Facebook and Twitter, concludes a study on online safety carried out by BitDefender.
Men are more likely than women to be deceived and fell into schemes of data theft when using social networks like Facebook and Twitter, concludes a study on online safety carried out by BitDefender.

 Fast, intuitive, and easy-to-manage computers designed to keep data and users safe while delivering all the power of the web.
Fast, intuitive, and easy-to-manage computers designed to keep data and users safe while delivering all the power of the web. 





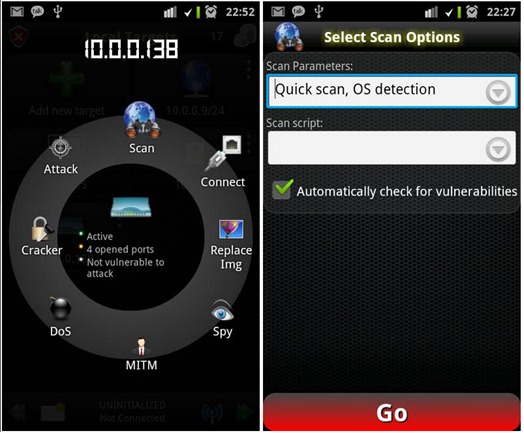
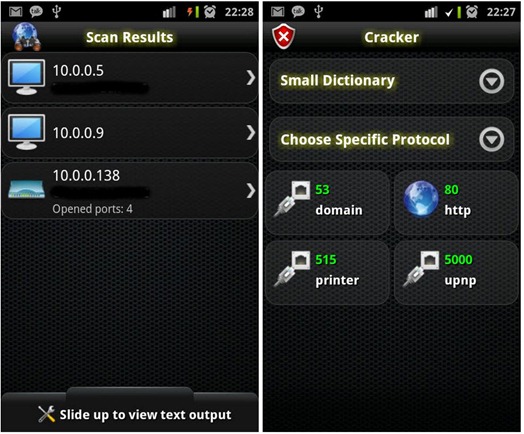
 Or they will, perhaps, when an app called Anti, or Android Network Toolkit, hits the Android market next week. The program, which Israeli security firm Zimperium revealed at the Defcon hacker conference in Las Vegas Friday and plans to make available to Android users in coming days, is designed for penetration testing–in theory, searching out and demonstrating vulnerabilities in computer systems so that they can be patched. Anti aims to bring all the hacking tools available to penetration testers on PCs to smartphones, with an automated interface intended to make sniffing local networks and owning remote servers as simple as pushing a few buttons.
Or they will, perhaps, when an app called Anti, or Android Network Toolkit, hits the Android market next week. The program, which Israeli security firm Zimperium revealed at the Defcon hacker conference in Las Vegas Friday and plans to make available to Android users in coming days, is designed for penetration testing–in theory, searching out and demonstrating vulnerabilities in computer systems so that they can be patched. Anti aims to bring all the hacking tools available to penetration testers on PCs to smartphones, with an automated interface intended to make sniffing local networks and owning remote servers as simple as pushing a few buttons. 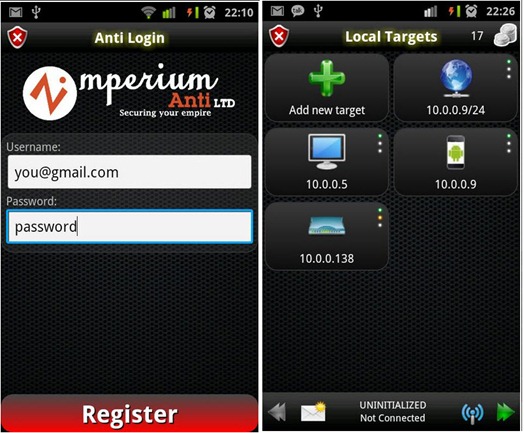








 With the opening of service to sex change in the area of Coimbra actress decided
With the opening of service to sex change in the area of Coimbra actress decided Like us on facebook:
Like us on facebook:  September 11, 2001. A day that will forever be remembered.
September 11, 2001. A day that will forever be remembered.






 Orange leaves his mark throughout history. Again.
Orange leaves his mark throughout history. Again.